RMM software that simplifies remote monitoring and management for hybrid work environments is no longer a luxury, but a necessity. The rise of hybrid work models has created complex IT landscapes, demanding solutions that can seamlessly manage devices and data across various locations and networks. This isn’t just about keeping things running smoothly; it’s about proactively addressing potential issues, bolstering security, and ultimately, enabling a productive and secure work experience for everyone, regardless of where they’re logging in from.
Let’s dive into how RMM software tackles these challenges head-on.
The shift to hybrid work has introduced a whole new set of IT headaches. Managing employees spread across offices, home offices, and co-working spaces requires a robust, adaptable solution. Enter RMM software, designed to provide a centralized platform for monitoring, managing, and securing all devices, no matter their location. From patching vulnerabilities to automating routine tasks, RMM offers a comprehensive approach to IT management in the modern hybrid world, enhancing productivity and minimizing downtime.
Defining Hybrid Work Environments and RMM Needs
The rise of hybrid work models has fundamentally reshaped the modern workplace. No longer confined to traditional office spaces, employees now seamlessly blend remote and on-site work, demanding a flexible and robust IT infrastructure to support their diverse needs. This necessitates a sophisticated approach to IT management, highlighting the critical role of Remote Monitoring and Management (RMM) software.Hybrid work environments are characterized by a dispersed workforce, utilizing a combination of office locations, remote home offices, and potentially even co-working spaces.
Employees connect to company resources using a variety of devices and network connections, creating a complex IT landscape. This complexity introduces unique challenges that traditional IT management strategies struggle to address effectively.
Challenges of Managing IT Infrastructure in Hybrid Work Models
Managing IT infrastructure in a hybrid work model presents several unique hurdles. Security concerns are amplified with employees accessing company data from diverse and potentially less secure locations. Troubleshooting technical issues becomes more complex, requiring remote diagnostic capabilities and efficient support mechanisms. Ensuring consistent performance and uptime across various network connections and devices adds another layer of complexity.
Furthermore, managing software updates, patching vulnerabilities, and enforcing security policies across a dispersed workforce requires sophisticated tools and processes. The lack of centralized control over devices and networks can lead to increased vulnerabilities and reduced productivity.
RMM Software Functionalities for Hybrid Work Environments
To effectively manage the complexities of a hybrid work environment, RMM software must offer a comprehensive suite of functionalities. Centralized device management allows IT administrators to monitor and control all company assets, regardless of location. Remote access and control capabilities enable IT support teams to quickly diagnose and resolve technical issues remotely, minimizing downtime and improving employee productivity.
Automated patching and software updates ensure that all devices are protected against the latest vulnerabilities, strengthening overall security. Robust security features, such as multi-factor authentication and endpoint protection, are essential to safeguard sensitive company data. Detailed reporting and analytics provide valuable insights into network performance, device health, and security posture, allowing for proactive identification and resolution of potential issues.
Finally, integrated help desk functionalities streamline support requests and improve the overall user experience.
Comparison of IT Infrastructure Management Needs
The table below compares the IT infrastructure management needs across on-premises, cloud, and hybrid environments.
| Feature | On-premises | Cloud | Hybrid |
|---|---|---|---|
| Hardware Management | Direct, physical access required | Minimal direct hardware management | Combination of direct and remote management |
| Software Deployment | On-site deployment and updates | Automated cloud-based deployment and updates | Hybrid approach combining on-site and cloud-based methods |
| Security Management | On-site security infrastructure and controls | Cloud-based security services and controls | Layered security approach combining on-site and cloud-based solutions |
| Monitoring and Alerting | Requires on-site monitoring tools | Centralized monitoring and alerting through cloud services | Combined on-site and cloud-based monitoring and alerting |
| Scalability | Limited scalability | Highly scalable | Scalability dependent on cloud and on-premises components |
| Cost | High initial investment, ongoing maintenance costs | Subscription-based model, potentially lower upfront costs | Cost varies depending on the balance between cloud and on-premises resources |
Core Features of RMM Software for Hybrid Environments
Managing a hybrid workforce presents unique IT challenges. The dispersed nature of employees, utilizing a mix of company-owned and personal devices, necessitates a robust and adaptable solution for remote monitoring and management. RMM software emerges as a crucial tool in navigating these complexities, offering a centralized platform to streamline IT operations and ensure business continuity.Remote monitoring capabilities are paramount in hybrid setups.
The lack of physical proximity to employees and their devices means that traditional IT support methods are insufficient. RMM software provides real-time visibility into the health and performance of all endpoints, regardless of location. This allows for quicker identification and resolution of issues, minimizing downtime and improving overall productivity.
Proactive Monitoring Features
Proactive monitoring is key to preventing problems before they impact users. Instead of reacting to reported issues, RMM software enables IT teams to anticipate and address potential problems. For instance, features like automated patch management ensure systems are updated with the latest security fixes, mitigating the risk of vulnerabilities. Disk space monitoring alerts administrators to low disk space on endpoints, preventing system crashes.
Real-time performance monitoring flags unusual activity or resource consumption, allowing for timely intervention. These proactive measures significantly reduce the risk of outages and improve overall system stability.
Automating Routine Tasks
Automating routine tasks through RMM software is crucial for efficiency in a hybrid environment. Tasks such as software deployment, updates, and security configurations can be automated, freeing up IT staff to focus on more strategic initiatives. For example, imagine deploying a new security application across hundreds of endpoints – RMM software can automate this process, ensuring consistent deployment and reducing the risk of human error.
Similarly, automated backups guarantee data protection, while automated scripting streamlines repetitive tasks, further optimizing IT workflows. This automation significantly reduces manual effort and improves operational efficiency.
Centralized Management and Reporting Dashboards
Centralized management and reporting dashboards provide a single pane of glass view of the entire IT infrastructure. This consolidated view simplifies the monitoring and management of all endpoints, regardless of their location or operating system. IT administrators can gain insights into system performance, security posture, and user activity through comprehensive reports. These dashboards provide a clear overview of the health of the IT environment, allowing for proactive problem-solving and informed decision-making.
The ability to generate customized reports helps in identifying trends, assessing the effectiveness of IT strategies, and justifying investments in technology.
Security Considerations in Hybrid RMM
Securing a hybrid workforce presents unique challenges. The dispersed nature of employees, coupled with the increased reliance on remote access and cloud services, expands the attack surface significantly. Traditional security measures are often insufficient to address the multifaceted threats inherent in this environment. A robust RMM solution is crucial for mitigating these risks and ensuring data protection.Hybrid work environments introduce a complex web of security threats.
Employees working from various locations, using diverse devices and networks, are more vulnerable to phishing attacks, malware infections, and unauthorized access. Unsecured home networks, public Wi-Fi hotspots, and personal devices introduce significant security gaps. Furthermore, managing access control and enforcing security policies across geographically dispersed teams becomes significantly more complex. Data breaches, resulting from compromised endpoints or weak security practices, can have severe financial and reputational consequences for organizations.
Security Features of Effective Hybrid RMM Solutions
Effective RMM solutions must incorporate a multi-layered security approach to address the unique challenges of hybrid work environments. These solutions should provide advanced endpoint protection, including real-time threat detection and response capabilities. Centralized patch management ensures that all devices are up-to-date with the latest security updates, minimizing vulnerabilities. Furthermore, robust access control mechanisms, such as multi-factor authentication (MFA), are essential to prevent unauthorized access to company resources.
Data encryption, both in transit and at rest, is critical for protecting sensitive information. Regular security audits and vulnerability assessments, automated through the RMM system, allow for proactive identification and mitigation of potential threats. Finally, comprehensive logging and reporting capabilities provide valuable insights into security events, enabling faster response times and improved incident management.
Designing a Security Policy for Hybrid Workforces Using RMM
A comprehensive security policy is paramount for safeguarding data and resources in a hybrid environment. This policy should clearly define acceptable use of company devices and networks, emphasizing secure password practices and the prohibition of unauthorized software. The policy should mandate the use of company-provided VPNs for remote access, ensuring all communications are encrypted. Regular security awareness training for employees is crucial, educating them about phishing scams, malware threats, and best practices for secure remote work.
The RMM system plays a central role in enforcing this policy. It can automate patch management, enforce security settings on endpoints, and provide real-time alerts for suspicious activity. The policy should also detail incident response procedures, specifying the steps to be taken in case of a security breach. Regular security audits, facilitated by the RMM system, ensure ongoing compliance with the policy.
The policy should also clearly Artikel the consequences of non-compliance.
Authentication and Authorization Methods for Remote Access
Choosing appropriate authentication and authorization methods is crucial for secure remote access. Password-based authentication, while convenient, is vulnerable to phishing and brute-force attacks. Multi-factor authentication (MFA), which requires multiple forms of verification (e.g., password, one-time code, biometric scan), significantly enhances security. Single sign-on (SSO) simplifies access management by allowing users to access multiple applications with a single set of credentials.
Role-based access control (RBAC) grants users access only to the resources they need to perform their job, minimizing the risk of unauthorized access. Certificate-based authentication offers strong security, using digital certificates to verify user identities. The selection of the most appropriate method depends on the organization’s specific security requirements and risk tolerance. A balanced approach, combining MFA with RBAC and potentially SSO, is often the most effective strategy for hybrid environments.
RMM software is a game-changer for managing hybrid work setups, streamlining device monitoring and troubleshooting from anywhere. Finding the right solution is key, especially for small businesses, and that’s where choosing from the best RMM software for small businesses with limited IT staff becomes crucial. Ultimately, selecting the right RMM simplifies remote management, boosting productivity and minimizing IT headaches in today’s flexible work environments.
For example, a financial institution might leverage certificate-based authentication combined with MFA for high-security applications, while a smaller business might opt for a simpler MFA solution integrated with SSO.
Integration and Scalability of RMM Solutions
In today’s dynamic hybrid work environment, choosing the right Remote Monitoring and Management (RMM) software is crucial. A robust solution isn’t just about managing devices; it’s about seamless integration with existing IT infrastructure and the ability to scale effortlessly as your organization grows. This section explores the vital aspects of integration and scalability in choosing an effective RMM system.
Key Integrations for Enhanced Functionality
Effective RMM solutions in hybrid environments aren’t standalone tools. Their power is amplified through integration with other critical IT systems. Seamless data flow between different platforms improves efficiency, streamlines workflows, and enhances overall IT management. For example, integrating your RMM with a ticketing system allows IT support teams to instantly receive alerts about device issues, automatically generate tickets, and track resolution progress, all within a centralized dashboard.
Managing a hybrid workforce? RMM software is your secret weapon, streamlining remote monitoring and management. Finding the right tools can be tricky, but thankfully, there are options out there; check out this guide on cost effective RMM tools for managed service providers to see what fits your budget. Ultimately, the right RMM solution will boost your efficiency and keep your hybrid team connected and productive.
Similarly, integration with security information and event management (SIEM) tools allows for proactive threat detection and response, improving overall security posture. Other valuable integrations include cloud storage services for efficient backup and recovery, and identity and access management (IAM) systems for enhanced security control.
Scalability: Adapting to Growth
Scalability is paramount for any RMM solution, particularly in a hybrid work environment where the number of managed devices and users can fluctuate rapidly. A scalable RMM solution should effortlessly handle increased workloads without compromising performance or security. This ensures that your IT team can efficiently manage a growing number of devices and users as your organization expands, both geographically and in terms of employee count.
A lack of scalability can lead to performance bottlenecks, increased management overhead, and potential security vulnerabilities. Consider companies like Zoom, which experienced massive growth during the pandemic. Their IT infrastructure, including RMM solutions, needed to adapt quickly to accommodate the sudden surge in users and devices, highlighting the importance of choosing a scalable solution from the outset.
Planning for Future Scalability
Choosing an RMM solution with a clear roadmap for future scalability is critical. This involves assessing your current needs and projecting your growth trajectory for the next 3-5 years, considering factors like employee growth, device proliferation, and anticipated technological advancements. Look for RMM vendors who offer flexible pricing models that adapt to your expanding needs, rather than those with rigid, per-device licensing that might become cost-prohibitive as your organization scales.
Cloud-based RMM solutions generally offer better scalability compared to on-premise solutions due to their inherent flexibility and capacity for dynamic resource allocation.
Factors to Consider When Evaluating RMM Scalability
Before committing to an RMM solution, thoroughly evaluate its scalability capabilities. Consider these key factors:
- Cloud-based vs. On-premise: Cloud-based solutions generally offer superior scalability due to their inherent flexibility and ability to handle increasing workloads.
- Pricing Model: Choose a flexible pricing model that scales with your needs, avoiding rigid per-device licensing that can become costly with growth.
- Vendor Reputation and Track Record: Research the vendor’s history and their ability to support large-scale deployments.
- API Integrations: Assess the availability of APIs to facilitate seamless integration with other IT systems.
- Performance Under Load: Test the RMM solution’s performance with simulated high workloads to ensure it can handle future growth.
- Technical Support and Documentation: Ensure the vendor provides robust technical support and comprehensive documentation to assist with scaling the solution.
User Experience and Support in Hybrid RMM

Managing a sprawling hybrid workforce requires an RMM solution that’s not just powerful, but also intuitive and supportive. The ideal user experience should seamlessly blend efficiency with ease of use, empowering IT administrators to handle complex tasks without getting bogged down in cumbersome interfaces. Effective support mechanisms are crucial, ensuring both administrators and end-users can quickly resolve issues and maximize the platform’s potential.A streamlined user experience is paramount for efficient remote monitoring and management.
This means intuitive dashboards, readily accessible information, and a design that minimizes the cognitive load on IT staff. Poor UX can lead to increased troubleshooting time, frustrated employees, and ultimately, a less secure IT environment.
Intuitive Dashboards and User-Friendly Interfaces
Effective RMM dashboards provide a consolidated view of the entire IT infrastructure, presenting critical information at a glance. Imagine a dashboard displaying a heatmap showing the real-time status of all devices, color-coded by operating system, security patch level, and overall health. Another section could showcase top alerts, prioritizing critical issues for immediate attention. This visual representation allows administrators to quickly identify potential problems and proactively address them before they escalate.
User-friendly interfaces should feature clear navigation, easily searchable device lists, and customizable views to cater to individual preferences and workflows. For example, a customizable dashboard might allow an administrator to prioritize alerts based on severity or device type, ensuring that critical issues are addressed first.
Effective Technical Support for Remote Users
Providing robust technical support to remote users is critical in a hybrid work environment. This involves a multi-pronged approach encompassing readily accessible self-service resources, efficient remote assistance tools, and proactive communication. A comprehensive knowledge base with FAQs, troubleshooting guides, and video tutorials can significantly reduce the need for direct support requests. Integration with remote assistance tools allows IT staff to directly access and troubleshoot user devices, resolving issues quickly and efficiently.
Proactive monitoring and alerts can identify potential problems before they impact users, minimizing disruptions and enhancing overall productivity. For instance, a system automatically detecting a low disk space alert on a user’s laptop and sending a proactive notification to the user, guiding them to free up space before performance issues arise, is a key aspect of effective support.
Onboarding New Users to the RMM System in a Hybrid Setup
Onboarding new users to the RMM system should be a straightforward and seamless process, minimizing disruption to both the user and the IT team.
- Pre-Onboarding Preparation: Before the user even starts, ensure the necessary software is installed and configured on their devices. This could include the RMM agent and any required security software.
- Automated Account Creation: Automate the process of creating user accounts, minimizing manual intervention. The system should automatically assign roles and permissions based on pre-defined templates.
- Guided Setup: Provide new users with a clear, step-by-step guide for setting up the RMM agent on their devices. This could include video tutorials or interactive walkthroughs.
- Initial Training and Support: Offer introductory training sessions or webinars to familiarize new users with the RMM system’s basic functionalities. Provide contact information for technical support and establish clear communication channels.
- Post-Onboarding Follow-up: Follow up with new users after onboarding to address any issues or questions and gauge their overall satisfaction with the system. This feedback can be used to continually improve the onboarding process.
Cost and ROI of RMM in Hybrid Work: RMM Software That Simplifies Remote Monitoring And Management For Hybrid Work Environments

Implementing and maintaining Remote Monitoring and Management (RMM) software for a hybrid work environment involves a careful consideration of costs and the potential return on investment. Understanding these factors is crucial for making an informed decision and justifying the expenditure to stakeholders. This section breaks down the cost components, explains ROI calculation, and provides a comparison of different RMM solutions to help you navigate this crucial aspect of adopting RMM technology.
Cost Components of RMM Implementation and Maintenance
The total cost of ownership (TCO) for RMM software goes beyond the initial license fee. Several ongoing costs contribute to the overall expense. These include the initial software license purchase, ongoing subscription fees (often tiered based on the number of devices managed), professional services for implementation and customization (if required), training costs for IT staff, and ongoing maintenance and support costs.
Unexpected costs can also arise from the need for additional hardware or software to integrate with the RMM platform. For example, a company might need to upgrade its network infrastructure to handle the increased data flow associated with remote monitoring. Accurate budgeting needs to consider all these factors.
Return on Investment (ROI) Calculation for RMM Solutions
Calculating the ROI of an RMM solution requires a clear understanding of both the costs and the benefits. The formula for ROI is simple:
(Return – Investment) / Investment100%
. The “return” represents the benefits realized from using the RMM software, while the “investment” represents the total cost of ownership. Quantifying the benefits can be challenging, but it’s crucial for a successful ROI calculation. For example, reduced help desk call resolution times, minimized downtime due to proactive monitoring, and improved security posture all contribute to the overall return.
A company can estimate these benefits based on historical data and projected improvements achieved through RMM implementation. For instance, if the company saves 10 hours of technician time per week at a cost of $50/hour, that’s a weekly return of $500, easily translating into annual savings.
Total Cost of Ownership (TCO) Comparison of RMM Solutions, RMM software that simplifies remote monitoring and management for hybrid work environments
The following table compares the TCO of three hypothetical RMM solutions, illustrating the variations in initial and ongoing costs, and ultimately, the estimated ROI. These figures are for illustrative purposes and should be replaced with data specific to your chosen RMM solutions and company context.
| RMM Solution | Initial Cost | Ongoing Costs (Annual) | Estimated ROI (3 years) |
|---|---|---|---|
| Solution A | $5,000 | $3,000 | 150% |
| Solution B | $2,000 | $4,500 | 120% |
| Solution C | $10,000 | $2,000 | 200% |
Key Metrics for Evaluating RMM Effectiveness
Tracking key metrics is vital for assessing the effectiveness of your RMM software and justifying its ongoing use. These metrics provide quantifiable data to demonstrate the value of the investment.
- Ticket Resolution Time: Measures the average time taken to resolve IT issues.
- Mean Time To Resolution (MTTR): Focuses on the average time to resolve critical incidents.
- Mean Time Between Failures (MTBF): Indicates the average time between system failures.
- System Uptime: Tracks the percentage of time systems are operational.
- Help Desk Ticket Volume: Monitors the number of support requests.
- Security Incident Response Time: Measures the time taken to respond to security threats.
- Cost Savings (e.g., reduced labor costs): Quantifies the financial benefits achieved through improved efficiency.
Case Studies
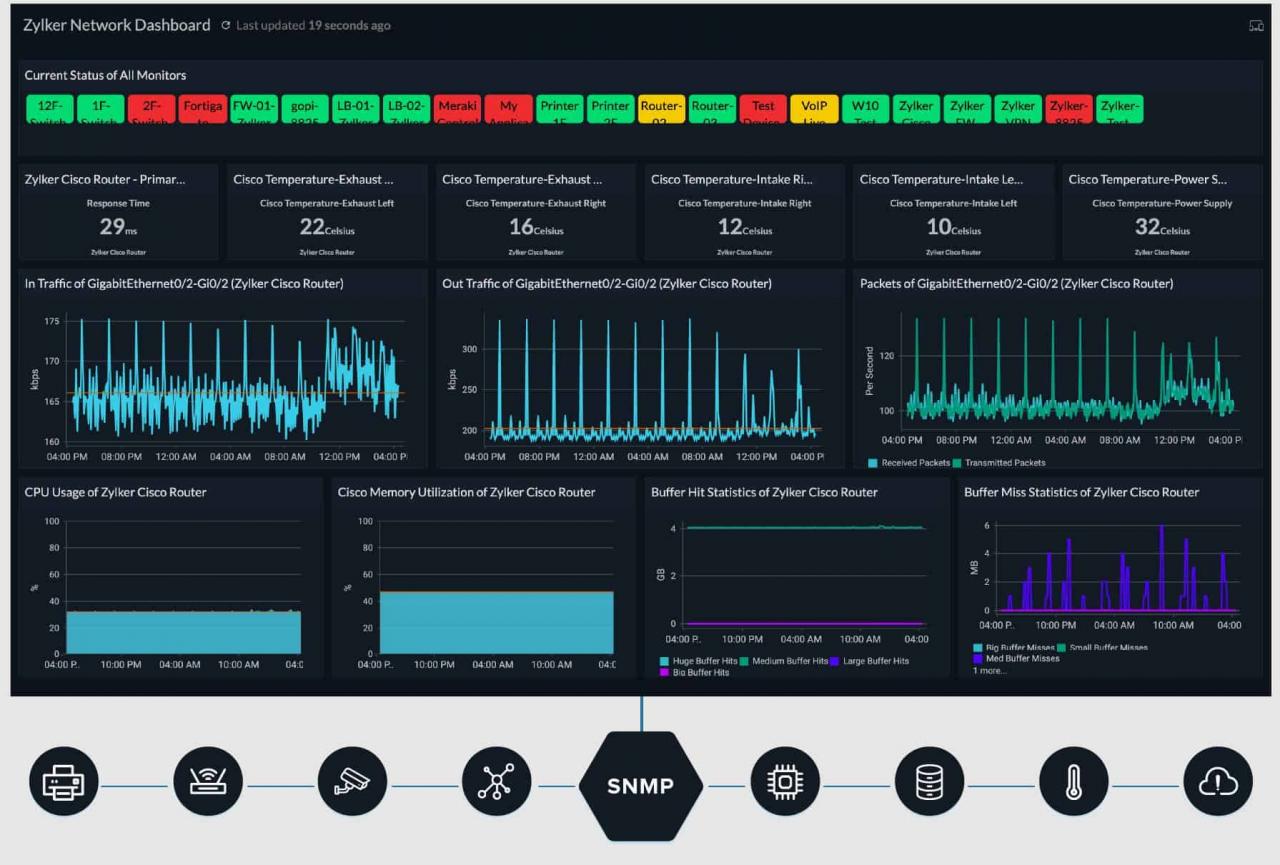
Real-world examples showcase the transformative power of RMM software in streamlining IT management for hybrid work environments. Seeing how others have successfully navigated the challenges of managing a dispersed workforce provides valuable insights and inspires confidence in adopting similar solutions. This section presents a hypothetical case study illustrating a successful RMM implementation, highlighting the benefits achieved and challenges overcome.
Successful Hybrid RMM Implementation at “InnovateTech”
InnovateTech, a rapidly growing software company, faced significant IT management challenges as they transitioned to a hybrid work model. Their previous system struggled to manage the diverse array of devices and locations, leading to slow response times for troubleshooting and increased security vulnerabilities. They decided to implement a comprehensive RMM solution to address these issues.
The initial challenge was integrating the RMM software with their existing IT infrastructure. This required careful planning and coordination with their IT team and the RMM vendor.
Another significant hurdle was training their IT staff on the new system. The vendor provided comprehensive training materials and ongoing support, which proved crucial in ensuring a smooth transition.
Finally, a key concern was data security, particularly given the increased number of remote access points. The chosen RMM solution offered robust security features, including multi-factor authentication and encryption, addressing these concerns effectively.
The implementation process took approximately three months, including planning, installation, training, and testing. The project was managed using agile methodologies, allowing for iterative improvements and adjustments based on feedback.
Benefits Observed After RMM Implementation
The successful implementation of the RMM system at InnovateTech yielded several key benefits:
- Improved Response Times: Troubleshooting and issue resolution times decreased significantly, leading to increased employee productivity and satisfaction. Previously, resolving a simple software issue could take hours; now, it’s often resolved within minutes.
- Enhanced Security Posture: The RMM solution’s robust security features significantly strengthened InnovateTech’s overall security posture, reducing the risk of data breaches and cyberattacks. Proactive monitoring and automated patching minimized vulnerabilities.
- Increased IT Efficiency: Automation of routine tasks, such as software updates and patch management, freed up IT staff to focus on more strategic initiatives, resulting in improved overall efficiency.
- Cost Savings: While there was an initial investment in the RMM software and implementation, the long-term cost savings from reduced downtime, improved security, and increased IT efficiency were substantial. InnovateTech estimated a 20% reduction in overall IT costs within the first year.
- Improved Employee Experience: Faster resolution of technical issues and improved system stability led to a more positive employee experience, boosting morale and productivity.