Evaluating RMM software for compliance with industry regulations is crucial in today’s complex regulatory landscape. From GDPR and CCPA to countless other industry-specific mandates, businesses face increasing pressure to ensure their IT infrastructure is secure and compliant. This guide delves into the key aspects of selecting and implementing RMM software that meets these stringent requirements, helping you navigate the complexities and build a robust, compliant system.
We’ll explore how to assess RMM solutions based on their security features, reporting capabilities, and integration with other compliance tools. We’ll also discuss the importance of vendor due diligence and ongoing monitoring to ensure your organization remains compliant with evolving regulations. By following the steps Artikeld here, you can significantly reduce your risk and build a more secure and compliant IT environment.
Understanding Regulatory Compliance Needs
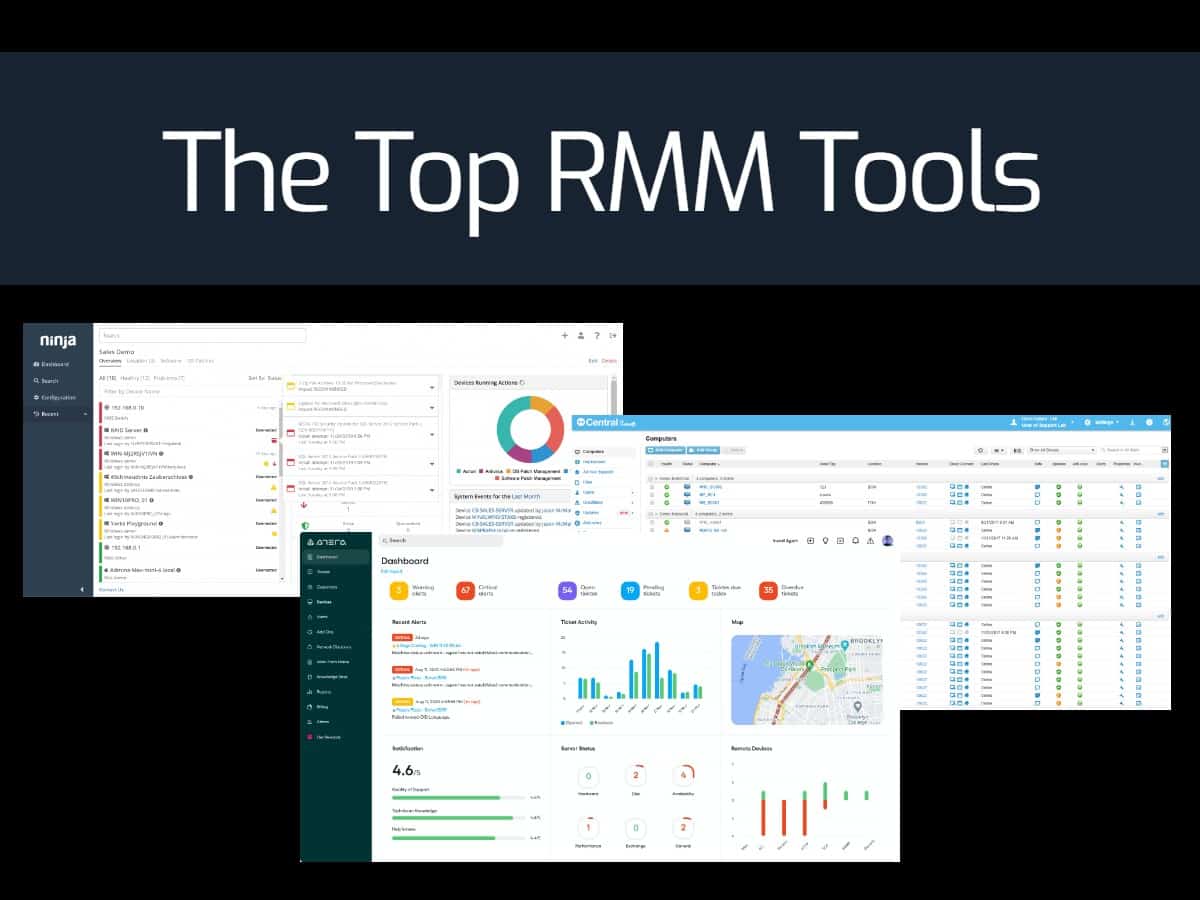
Choosing the right RMM (Remote Monitoring and Management) software isn’t just about features and functionality; it’s crucial to ensure it aligns with your organization’s regulatory compliance obligations. Failing to do so can lead to hefty fines, reputational damage, and loss of customer trust. This section delves into the key regulatory considerations when selecting an RMM solution.
Key Industry Regulations Impacting RMM Software Selection
Several regulations significantly impact the selection of RMM software. These regulations often overlap, demanding a multifaceted approach to compliance. For example, the Health Insurance Portability and Accountability Act (HIPAA) in the US governs the protection of patient health information, requiring stringent security measures for any software handling such data. Similarly, the Payment Card Industry Data Security Standard (PCI DSS) dictates security requirements for organizations handling credit card information.
In the European Union, the General Data Protection Regulation (GDPR) sets a high bar for data protection, influencing RMM software choices globally due to its broad reach. Finally, industry-specific regulations, such as those in finance or healthcare, further refine these requirements. The complexity necessitates a thorough understanding of all applicable regulations before selecting an RMM solution.
Data Privacy Compliance Requirements
Data privacy is paramount, and RMM software plays a vital role in its protection. The GDPR and the California Consumer Privacy Act (CCPA) are two prominent examples of legislation demanding robust data protection measures. GDPR mandates organizations to obtain explicit consent for data processing, ensure data security, and provide individuals with the right to access, rectify, and erase their personal data.
CCPA, while focusing on California residents, mirrors many GDPR principles, requiring similar levels of transparency and control over personal information. Compliance necessitates RMM software that offers features like data encryption both in transit and at rest, robust access controls, and comprehensive data logging capabilities to demonstrate compliance. Failure to meet these requirements can result in severe penalties.
Importance of Audit Trails and Reporting Capabilities
Audit trails and robust reporting capabilities are essential for demonstrating compliance with regulatory standards. A comprehensive audit trail provides an irrefutable record of all actions performed within the RMM system, including user access, data modifications, and security events. This is critical for investigations, security audits, and demonstrating compliance to regulatory bodies. Detailed reporting features allow organizations to easily generate reports showcasing their adherence to compliance requirements, providing evidence of effective security practices and data protection measures.
These features are crucial for meeting regulatory requirements and mitigating potential risks.
Compliance Certifications and RMM Platform Comparison
The following table compares the compliance certifications, data encryption methods, and audit trail features of several popular RMM platforms. Note that certifications and features can change, so always verify directly with the vendor.
| Platform Name | Certifications Held | Data Encryption Methods | Audit Trail Features |
|---|---|---|---|
| Platform A | ISO 27001, SOC 2 Type II | AES-256 encryption in transit and at rest | Detailed logs of all user actions, security events, and data modifications |
| Platform B | SOC 2 Type II | AES-256 encryption in transit and at rest; TLS 1.2+ | Comprehensive audit trails with customizable reporting options |
| Platform C | ISO 27001 | AES-256 encryption at rest; TLS 1.3+ for transit | Real-time audit logging with alerts for suspicious activity |
| Platform D | HIPAA compliant | AES-256 encryption in transit and at rest | Detailed audit trails with granular access control |
Evaluating RMM Security Features
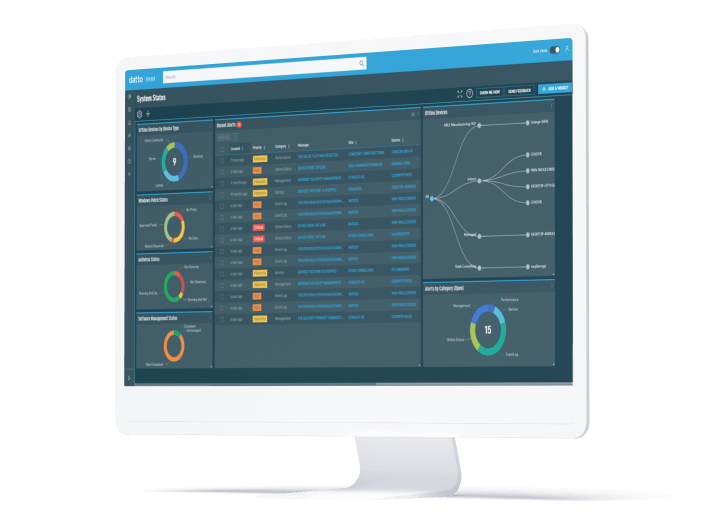
Choosing the right RMM (Remote Monitoring and Management) software is crucial, especially when considering regulatory compliance. Beyond basic functionality, the security features of your RMM are paramount to protecting sensitive data and maintaining compliance with industry standards like HIPAA, GDPR, and CCPA. A robust security posture is not just a box to tick; it’s the foundation upon which your entire compliance strategy rests.
Access Control and User Permissions
Effective access control is the cornerstone of a secure RMM system. It dictates who can access what data and perform which actions within the system. Granular user permissions ensure that only authorized personnel have access to specific functionalities and data sets, preventing unauthorized access and data breaches. For instance, a technician might have access to manage client devices but not to view sensitive financial information, while a manager might have broader administrative privileges.
Evaluating RMM software for compliance hinges on several key factors, including robust security features. A critical aspect of this is ensuring timely patching of vulnerabilities, which is why choosing an RMM solution with strong patch management features, like those discussed in this helpful guide choosing an RMM solution with strong patch management features , is paramount. Ultimately, a comprehensive patching strategy directly contributes to your overall regulatory compliance and minimizes security risks.
Implementing the principle of least privilege—granting users only the minimum necessary access—is a best practice for minimizing risk. Regular audits of user permissions are vital to ensure they remain aligned with current roles and responsibilities.
Data Encryption: In Transit and At Rest
Data encryption is a critical security measure that safeguards sensitive information. Encryption in transit protects data while it’s being transmitted between devices and servers, using protocols like TLS/SSL. Encryption at rest protects data stored on servers and databases, utilizing strong encryption algorithms. Imagine a scenario where an RMM system stores client health records. Without encryption, a data breach could expose this sensitive information.
However, with robust encryption both in transit and at rest, even if a breach occurs, the data remains unreadable to unauthorized individuals. Leading RMM solutions typically support AES-256 encryption, considered a highly secure standard.
Authentication Methods: MFA and SSO
Strong authentication methods are essential for preventing unauthorized access. Multi-factor authentication (MFA) adds an extra layer of security beyond just a password, often involving a one-time code from a mobile app or email. Single sign-on (SSO) allows users to access multiple applications with a single set of credentials, streamlining access while improving security by reducing the number of passwords to manage.
Implementing MFA and SSO reduces the risk of unauthorized access significantly, as even if a password is compromised, the attacker would still need access to the second factor to gain entry. This is particularly critical for meeting compliance requirements that mandate strong authentication practices.
Security Protocols Supported by Leading RMM Solutions
Many leading RMM solutions support a range of security protocols to enhance their security posture and aid compliance. For example, support for protocols like TLS 1.3, SSH, and robust firewall configurations are common. These protocols provide secure communication channels, protect against unauthorized access, and help maintain data integrity. The specific protocols supported will vary depending on the RMM vendor, but reviewing this information is critical during the evaluation process.
Choosing an RMM solution with a comprehensive suite of security protocols is crucial for achieving and maintaining regulatory compliance.
Assessing RMM Reporting and Auditing Capabilities: Evaluating RMM Software For Compliance With Industry Regulations
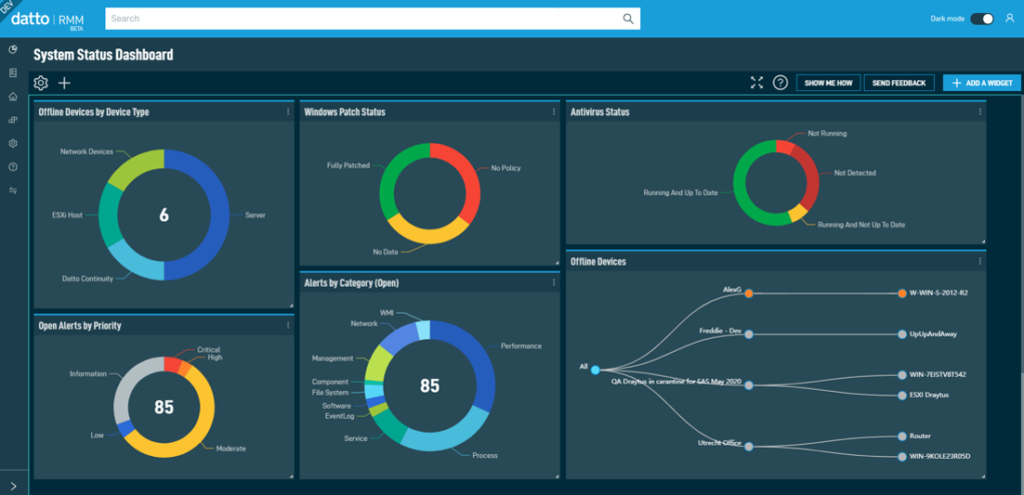
Effective RMM reporting and auditing are crucial for demonstrating regulatory compliance. A robust system provides the necessary evidence to auditors, ensuring your organization meets the requirements of relevant standards and avoids potential penalties. This section explores the key aspects of leveraging RMM for comprehensive compliance reporting and auditing.
Designing a Comprehensive Audit Trail Report
A comprehensive audit trail report should meticulously document all significant system activities relevant to compliance. This includes user actions, software deployments, security configuration changes, and any events that could impact data integrity or security. The report needs to be easily searchable and filterable, allowing quick access to specific events based on date, user, or action type. For example, a report detailing all changes to access control lists (ACLs) on critical servers over the past 90 days would be crucial for demonstrating adherence to access control policies mandated by regulations like HIPAA or GDPR.
The report should clearly indicate the timestamp, user involved, action performed, and any relevant details such as the specific files or systems affected. The format should be easily exportable to common formats like CSV or PDF for review and submission to auditors.
Best Practices for Configuring RMM Systems to Generate Compliant Audit Logs
Proper configuration of your RMM system is paramount for generating audit logs that meet regulatory standards. This involves enabling detailed logging for all critical system functions, defining appropriate log retention policies, and ensuring the logs are tamper-proof and securely stored. Implementing multi-factor authentication (MFA) for all users accessing the RMM system is also crucial to prevent unauthorized modifications to logs.
Regularly reviewing the RMM system’s configuration settings to ensure they remain aligned with evolving regulatory requirements and best practices is essential. For instance, configuring the RMM to log all failed login attempts can help detect and prevent potential security breaches. Furthermore, encrypting audit logs both in transit and at rest is a vital security measure, ensuring data confidentiality and integrity.
Key Metrics for Regulatory Compliance Reporting
Tracking and reporting key metrics is essential for monitoring compliance status and identifying potential gaps. These metrics should be tailored to the specific regulations applicable to your organization. Examples include: the number of security vulnerabilities detected and remediated, the number of successful and failed login attempts, the frequency of security configuration changes, and the average time taken to respond to security incidents.
Regular reporting on these metrics, perhaps on a monthly or quarterly basis, allows for proactive identification and resolution of compliance issues before they escalate. For instance, a consistent high number of failed login attempts might indicate a weakness in password policies requiring immediate attention. Visualizing these metrics using dashboards and charts can facilitate quick identification of trends and potential risks.
Choosing the right RMM software is crucial, especially when ensuring compliance with strict industry regulations. The key is understanding the long-term impact of your tech investments, much like learning to measuring the ROI of CRM investments and demonstrating business value teaches. This same principle applies to RMM; a thorough evaluation helps justify the cost and ensures your business stays ahead of the compliance curve.
Using RMM Reporting to Identify and Address Compliance Gaps
RMM reporting features provide valuable insights into potential compliance gaps. By analyzing the generated reports, organizations can identify areas needing improvement. For example, identifying a significant number of unpatched systems might indicate a deficiency in the patch management process. Similarly, an increase in security alerts might signal a need for enhanced security monitoring and incident response capabilities. The RMM system should allow for easy filtering and sorting of data to isolate specific areas of concern.
This allows for targeted remediation efforts, focusing resources where they are most needed. Regularly reviewing reports and taking prompt action on identified gaps ensures ongoing compliance and minimizes the risk of non-compliance penalties.
Vendor Due Diligence and Contractual Obligations
Choosing the right RMM vendor isn’t just about features; it’s about ensuring ongoing compliance with ever-evolving regulations. A thorough due diligence process and a robust contract are crucial for mitigating risk and maintaining a secure IT environment. This section explores key questions to ask vendors, essential contractual clauses, and a checklist to verify their compliance claims.
Understanding a vendor’s approach to compliance is paramount. This involves examining their internal processes, certifications, and commitment to staying ahead of regulatory changes. The information gathered will inform your decision-making process and allow for a more secure partnership.
Key Questions for RMM Vendors Regarding Compliance Practices
Asking the right questions is crucial for understanding a vendor’s commitment to compliance. These inquiries should delve into their security practices, certifications, and incident response plans, ensuring transparency and accountability.
- Vendor’s documented compliance program details, including specific regulations addressed (e.g., SOC 2, ISO 27001, HIPAA).
- Details on their security certifications and audits, including dates and relevant reports.
- Information about their incident response plan and procedures in case of a data breach.
- Description of their data backup and recovery procedures, ensuring data integrity and availability.
- Explanation of their employee background checks and security training programs.
Essential Contractual Clauses for Ongoing Compliance
The contract should clearly define responsibilities and expectations regarding compliance. These clauses are crucial for protecting your organization and ensuring the vendor’s accountability.
- Specific regulatory compliance obligations the vendor must meet (e.g., adherence to HIPAA, GDPR, CCPA).
- Details on data security practices, including encryption methods, access controls, and data breach notification procedures.
- Clear definition of data ownership and responsibility, outlining who is accountable for data breaches.
- Clause outlining the vendor’s obligation to maintain compliance with all applicable regulations throughout the contract term.
- Specification of audit rights, allowing your organization to independently verify the vendor’s compliance efforts.
Comparison of Vendor Approaches to Ongoing Compliance
Vendors adopt different approaches to ensure ongoing compliance. Some may rely heavily on certifications, while others may emphasize internal processes and regular audits. Understanding these differences is crucial for selecting a vendor aligned with your risk tolerance.
For example, Vendor A might boast numerous certifications and regular third-party audits, providing a strong external validation of their compliance efforts. In contrast, Vendor B might emphasize its robust internal security team and continuous monitoring processes, focusing on proactive risk management. Both approaches can be effective, but their strengths lie in different areas.
Due Diligence Checklist for Verifying Vendor Claims, Evaluating RMM software for compliance with industry regulations
Verifying vendor claims requires a structured approach. This checklist helps ensure you gather the necessary evidence to support their compliance assertions.
- Request and review the vendor’s security certifications and audit reports.
- Independently verify the validity of their certifications through the issuing organizations.
- Conduct a thorough review of their security policies and procedures.
- Request references from other clients and inquire about their experience with the vendor’s compliance practices.
- Assess the vendor’s incident response plan and its effectiveness in handling security incidents.
Integration with Other Compliance Tools
Choosing an RMM solution shouldn’t be a siloed decision. Effective compliance hinges on a holistic security posture, demanding seamless integration between your RMM and other critical security and compliance tools. A robust RMM platform should act as a central nervous system, aggregating data and streamlining workflows across your entire security ecosystem. This interconnectedness enhances efficiency, reduces redundancies, and ultimately strengthens your organization’s compliance posture.RMM integration isn’t just about convenience; it’s about maximizing the value of your existing security investments.
By connecting your RMM with other tools, you gain a unified view of your IT environment, allowing for proactive risk management and more efficient incident response. This interconnected approach minimizes blind spots and allows for faster, more informed decision-making, crucial for maintaining compliance in today’s dynamic threat landscape.
Integration with Vulnerability Management Systems
Integrating your RMM with a vulnerability management system (VMS) significantly improves your ability to identify and remediate security vulnerabilities across your managed endpoints. The RMM can automatically discover and inventory assets, while the VMS performs vulnerability scans. Once vulnerabilities are identified, the RMM can then be used to deploy patches, configure security settings, or even isolate affected systems, all within a streamlined workflow.
This automated approach accelerates remediation, reducing your overall risk exposure and demonstrating a proactive approach to compliance. For example, integrating an RMM like Datto RMM with a VMS like QualysGuard allows for automated patch deployment based on identified vulnerabilities, minimizing the window of exposure. This integrated approach ensures that critical security patches are applied swiftly, satisfying regulatory requirements demanding timely vulnerability remediation.
Integration with Incident Management Systems
Integrating your RMM with an incident management system (IMS) provides a centralized platform for managing security incidents. When a security incident occurs, the RMM can automatically alert the IMS, providing key context such as affected systems, user accounts, and potential impact. The IMS then facilitates the incident response process, allowing for efficient tracking, communication, and remediation. This integrated approach reduces response times, minimizes disruption, and ensures compliance with incident reporting requirements.
Imagine a scenario where a ransomware attack is detected. The RMM can automatically isolate the infected systems, preventing further spread, while simultaneously triggering an alert in the IMS, initiating the incident response plan. This integrated approach minimizes the impact of the attack and demonstrates a robust incident response capability, crucial for compliance. This integrated workflow, for example, using ServiceNow as the IMS, ensures a swift and documented response to any security incident, streamlining compliance reporting.
Workflow Example: Seamless RMM Integration
Consider a scenario where a vulnerability scan reveals a critical vulnerability on a server. The VMS identifies the vulnerability and automatically creates a ticket within the RMM. The RMM then uses this information to automatically deploy a patch to the server. Upon successful patch deployment, the RMM updates the ticket status and sends a notification to the security team.
If the patch fails, an escalation process is triggered within the RMM, creating a ticket in the IMS to initiate a manual remediation process. This automated and integrated workflow ensures timely remediation of vulnerabilities, while maintaining a clear audit trail for compliance purposes. This approach significantly streamlines the entire process, improving efficiency and reducing the likelihood of compliance violations.
Ongoing Monitoring and Remediation
Maintaining regulatory compliance isn’t a one-time task; it’s an ongoing process. Effective RMM software plays a crucial role in this, allowing for proactive identification and resolution of compliance issues. This section details best practices for continuous monitoring and efficient remediation strategies.Proactive compliance management, facilitated by robust RMM tools, minimizes risks and ensures consistent adherence to industry regulations. By leveraging automated alerts, regular audits, and streamlined workflows, organizations can significantly reduce the burden of manual checks and enhance overall security posture.
This approach allows for a more agile response to evolving regulatory landscapes and potential vulnerabilities.
RMM System Monitoring Best Practices
Regular monitoring of your RMM system is paramount to maintaining compliance. This involves scheduled checks of security configurations, patch management status, and the overall health of managed endpoints. Setting up automated alerts for critical events, such as failed security audits or unauthorized access attempts, ensures timely intervention. Regular review of these alerts and system logs is essential to identify and address potential compliance violations promptly.
This proactive approach prevents minor issues from escalating into major breaches, significantly reducing the risk of non-compliance. For example, a scheduled check revealing outdated antivirus software on several endpoints would trigger an immediate remediation process, preventing a potential vulnerability.
Proactive Identification and Resolution of Compliance Issues
RMM tools offer powerful capabilities for proactively identifying and addressing compliance issues. Automated vulnerability scanning, combined with patch management features, allows for the quick identification and remediation of known vulnerabilities. Regular security audits, performed through the RMM system, highlight areas needing attention. By integrating the RMM with other compliance tools, organizations can gain a holistic view of their security posture and identify potential compliance gaps.
Imagine an RMM system automatically detecting a missing security patch on a server. The system then automatically schedules and executes the patch installation, generating a report documenting the entire process. This automated workflow ensures compliance is maintained with minimal manual intervention.
Responding to Compliance Audits and Addressing Deficiencies
Responding to compliance audits efficiently requires well-documented processes and readily available data. RMM systems provide the necessary tools to gather and present audit evidence quickly. This includes generating reports on system configurations, patch management history, and security event logs. If deficiencies are identified during an audit, the RMM system helps prioritize remediation efforts by highlighting the most critical vulnerabilities.
A detailed plan, outlining steps for addressing each deficiency, should be created and documented. The RMM system can then be used to track progress and ensure all identified issues are resolved. For example, if an audit reveals insufficient password complexity, the RMM can be used to enforce a new, stronger password policy across all managed devices.
Remediation Flowchart
The following flowchart illustrates the steps involved in remediating compliance issues identified through RMM monitoring:[Imagine a flowchart here. The flowchart would begin with “Compliance Issue Identified (via RMM)”, branching to “Issue Assessment & Prioritization”. This would lead to “Develop Remediation Plan”, followed by “Implement Remediation”. Next would be “Verification & Validation”, leading to either “Issue Resolved” or “Re-evaluate & Iterate”.
The “Issue Resolved” branch would conclude with “Document Remediation”, while the “Re-evaluate & Iterate” branch would loop back to “Issue Assessment & Prioritization”. Each step would be visually represented by a box, with arrows showing the flow between steps.]